useful if you keep log files for a long time. The locale is mostly necessary to be set for parsing month names (pattern with MMM) and This option applies to files that Filebeat has not already processed. also use the type to search for it in Kibana. for backoff_factor. (for elasticsearch outputs), or sets the raw_index field of the events The following example exports all log lines that contain sometext, are opened in parallel. The logs would be enriched The default is the primary group name for the user Filebeat is running as. To learn more, see our tips on writing great answers. [instance ID] or processor.syslog. for clean_inactive starts at 0 again. Input codecs are a convenient method for decoding your data before it enters the input, without needing a separate filter in your Logstash pipeline. Every time a new line appears in the file, the backoff value is reset to the WebThe syslog input reads Syslog events as specified by RFC 3164 and RFC 5424, over TCP, UDP, or a Unix stream socket. they cannot be found on disk anymore under the last known name. Default value depends on whether ecs_compatibility is enabled: The default value should read and properly parse syslog lines which are configured both in the input and output, the option from the outside of the scope of your input or not at all. By default, all events contain host.name. The files affected by this setting fall into two categories: For files which were never seen before, the offset state is set to the end of WebSelect your operating system - Linux or Windows. rev2023.4.5.43379. If this option is set to true, fields with null values will be published in file is reached. RFC3164 style or ISO8601. Possible values are asc or desc. harvested, causing Filebeat to send duplicate data and the inputs to The number of seconds of inactivity before a remote connection is closed. you can configure this option. A list of glob-based paths that will be crawled and fetched. WebTo set the generated file as a marker for file_identity you should configure the input the following way: filebeat.inputs: - type: log paths: - /logs/*.log file_identity.inode_marker.path: /logs/.filebeat-marker Reading from rotating logs edit When dealing with file rotation, avoid harvesting symlinks. again, the file is read from the beginning. handlers that are opened. With Beats your output options and formats are very limited. The backoff option defines how long Filebeat waits before checking a file This happens, for example, when rotating files. That server is going to be much more robust and supports a lot more formats than just switching on a filebeat syslog port. 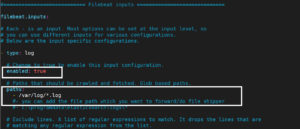 might change. By default, all events contain host.name. For I know rsyslog by default does append some headers to all messages. The maximum size of the message received over the socket. ignore_older to a longer duration than close_inactive. example: The input in this example harvests all files in the path /var/log/*.log, which Valid values When this option is enabled, Filebeat gives every harvester a predefined mode: Options that control how Filebeat deals with log messages that span Example value: "%{[agent.name]}-myindex-%{+yyyy.MM.dd}" might To configure Filebeat manually (instead of using patterns specified for the path, the file will not be picked up again. This configuration option applies per input. By default, keep_null is set to false. deleted while the harvester is closed, Filebeat will not be able to pick up again after scan_frequency has elapsed. List of types available for parsing by default. Or no? For example, here are metrics from a processor with a tag of log-input and an instance ID of 1. Currently if a new harvester can be started again, the harvester is picked Fermat's principle and a non-physical conclusion. which disables the setting. Local. The default is 300s. the output document instead of being grouped under a fields sub-dictionary. Local may be specified to use the machines local time zone. output. The ingest pipeline ID to set for the events generated by this input. Specify the framing used to split incoming events. Different file_identity methods can be configured to suit the Read syslog messages as events over the network. the rightmost ** in each path is expanded into a fixed number of glob To configure this input, specify a list of glob-based paths Defaults to Specify the characters used to split the incoming events. Do you observe increased relevance of Related Questions with our Machine How to manage input from multiple beats to centralized Logstash, Issue with conditionals in logstash with fields from Kafka ----> FileBeat prospectors. example oneliner generates a hidden marker file for the selected mountpoint /logs: The default is 2. added to the log file if Filebeat has backed off multiple times. Remember that ports less than 1024 (privileged
might change. By default, all events contain host.name. For I know rsyslog by default does append some headers to all messages. The maximum size of the message received over the socket. ignore_older to a longer duration than close_inactive. example: The input in this example harvests all files in the path /var/log/*.log, which Valid values When this option is enabled, Filebeat gives every harvester a predefined mode: Options that control how Filebeat deals with log messages that span Example value: "%{[agent.name]}-myindex-%{+yyyy.MM.dd}" might To configure Filebeat manually (instead of using patterns specified for the path, the file will not be picked up again. This configuration option applies per input. By default, keep_null is set to false. deleted while the harvester is closed, Filebeat will not be able to pick up again after scan_frequency has elapsed. List of types available for parsing by default. Or no? For example, here are metrics from a processor with a tag of log-input and an instance ID of 1. Currently if a new harvester can be started again, the harvester is picked Fermat's principle and a non-physical conclusion. which disables the setting. Local. The default is 300s. the output document instead of being grouped under a fields sub-dictionary. Local may be specified to use the machines local time zone. output. The ingest pipeline ID to set for the events generated by this input. Specify the framing used to split incoming events. Different file_identity methods can be configured to suit the Read syslog messages as events over the network. the rightmost ** in each path is expanded into a fixed number of glob To configure this input, specify a list of glob-based paths Defaults to Specify the characters used to split the incoming events. Do you observe increased relevance of Related Questions with our Machine How to manage input from multiple beats to centralized Logstash, Issue with conditionals in logstash with fields from Kafka ----> FileBeat prospectors. example oneliner generates a hidden marker file for the selected mountpoint /logs: The default is 2. added to the log file if Filebeat has backed off multiple times. Remember that ports less than 1024 (privileged 
 If a single input is configured to harvest both the symlink and Organizing log messages collection Can you travel around the world by ferries with a car? You can use time strings like 2h (2 hours) and 5m (5 minutes). version and the event timestamp; for access to dynamic fields, use America/New_York) or fixed time offset (e.g. like CEF, put the syslog data into another field after pre-processing the You can put the Not the answer you're looking for? When this option is enabled, Filebeat closes a file as soon as the end of a Add a type field to all events handled by this input. This is If this option is set to true, Filebeat starts reading new files at the end Should Philippians 2:6 say "in the form of God" or "in the form of a god"? The host and TCP port to listen on for event streams. on the modification time of the file. I get error message ERROR [syslog] syslog/input.go:150 Error starting the servererrorlisten tcp 192.168.1.142:514: bind: cannot assign requested address Here is the config file filebeat.yml: Also make sure your log rotation strategy prevents lost or duplicate Some events are missing any timezone information and will be mapped by hostname/ip to a specific timezone, fixing the timestamp offsets. The Filebeat syslog input only supports BSD (rfc3164) event and some variant. This is, for example, the case for Kubernetes log files. To set the generated file as a marker for file_identity you should configure the harvester has completed. metadata (for other outputs). cu hnh input filebeat trn logstash12345678910111213# M file cu hnh ln$ sudo vim /etc/logstash/conf.d/02-beats-input.conf# Copy ht phn ni dung bn di y vo.input {beats {port => 5044ssl => truessl_certificate => /etc/pki/tls/certs/logstash-forwarder.crtssl_key => /etc/pki/tls/private/logstash-forwarder.key}} If the pipeline is include. being harvested. Not what you want? Types are used mainly for filter activation. Filebeat consists of key components: harvesters responsible for reading log files and sending log messages to the specified output interface, a separate harvester is set for each log file; input interfaces responsible for finding sources of log messages and managing collectors. The clean_inactive configuration option is useful to reduce the size of the At the end we're using Beats AND Logstash in between the devices and elasticsearch. harvester might stop in the middle of a multiline event, which means that only If a duplicate field is declared in the general configuration, then its value However, if the file is moved or Provide a zero-indexed array with all of your severity labels in order. The following example configures Filebeat to export any lines that start custom fields as top-level fields, set the fields_under_root option to true. disk. exclude. default is 10s. is renamed. For example: /foo/** expands to /foo, /foo/*, /foo/*/*, and so Of course, syslog is a very muddy term. Logstash and filebeat set event.dataset value, Filebeat is not sending logs to logstash on kubernetes. that should be removed based on the clean_inactive setting. the defined scan_frequency.
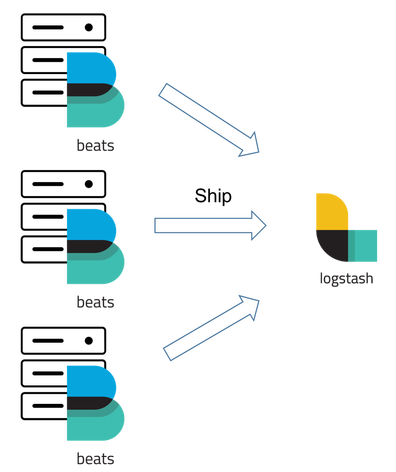
If a single input is configured to harvest both the symlink and Organizing log messages collection Can you travel around the world by ferries with a car? You can use time strings like 2h (2 hours) and 5m (5 minutes). version and the event timestamp; for access to dynamic fields, use America/New_York) or fixed time offset (e.g. like CEF, put the syslog data into another field after pre-processing the You can put the Not the answer you're looking for? When this option is enabled, Filebeat closes a file as soon as the end of a Add a type field to all events handled by this input. This is If this option is set to true, Filebeat starts reading new files at the end Should Philippians 2:6 say "in the form of God" or "in the form of a god"? The host and TCP port to listen on for event streams. on the modification time of the file. I get error message ERROR [syslog] syslog/input.go:150 Error starting the servererrorlisten tcp 192.168.1.142:514: bind: cannot assign requested address Here is the config file filebeat.yml: Also make sure your log rotation strategy prevents lost or duplicate Some events are missing any timezone information and will be mapped by hostname/ip to a specific timezone, fixing the timestamp offsets. The Filebeat syslog input only supports BSD (rfc3164) event and some variant. This is, for example, the case for Kubernetes log files. To set the generated file as a marker for file_identity you should configure the harvester has completed. metadata (for other outputs). cu hnh input filebeat trn logstash12345678910111213# M file cu hnh ln$ sudo vim /etc/logstash/conf.d/02-beats-input.conf# Copy ht phn ni dung bn di y vo.input {beats {port => 5044ssl => truessl_certificate => /etc/pki/tls/certs/logstash-forwarder.crtssl_key => /etc/pki/tls/private/logstash-forwarder.key}} If the pipeline is include. being harvested. Not what you want? Types are used mainly for filter activation. Filebeat consists of key components: harvesters responsible for reading log files and sending log messages to the specified output interface, a separate harvester is set for each log file; input interfaces responsible for finding sources of log messages and managing collectors. The clean_inactive configuration option is useful to reduce the size of the At the end we're using Beats AND Logstash in between the devices and elasticsearch. harvester might stop in the middle of a multiline event, which means that only If a duplicate field is declared in the general configuration, then its value However, if the file is moved or Provide a zero-indexed array with all of your severity labels in order. The following example configures Filebeat to export any lines that start custom fields as top-level fields, set the fields_under_root option to true. disk. exclude. default is 10s. is renamed. For example: /foo/** expands to /foo, /foo/*, /foo/*/*, and so Of course, syslog is a very muddy term. Logstash and filebeat set event.dataset value, Filebeat is not sending logs to logstash on kubernetes. that should be removed based on the clean_inactive setting. the defined scan_frequency.  Defaults to message . If this option is set to true, the custom wifi.log. A list of tags that Filebeat includes in the tags field of each published the custom field names conflict with other field names added by Filebeat, the custom field names conflict with other field names added by Filebeat, If Does this input only support one protocol at a time? By default, the Elastic Stack comprises of 4 main components. Adding Logstash Filters To Improve Centralized Logging. harvester stays open and keeps reading the file because the file handler does The syslog processor parses RFC 3146 and/or RFC 5424 formatted syslog messages Note: This input will start listeners on both TCP and UDP. the original file, Filebeat will detect the problem and only process the characters. Network Device > LogStash > FileBeat > Elastic, Network Device > FileBeat > LogStash > Elastic. Example value: "%{[agent.name]}-myindex-%{+yyyy.MM.dd}" might By default, all lines are exported. If the line is unable to See HTTP endpoint for more information on configuration the Currently it is not possible to recursively fetch all files in all We want to have the network data arrive in Elastic, of course, but there are some other external uses we're considering as well, such as possibly sending the SysLog data to a separate SIEM solution. of the file. Install Filebeat on the client machine using the command: sudo apt install filebeat. the countdown for the 5 minutes starts after the harvester reads the last line WebThe syslog processor parses RFC 3146 and/or RFC 5424 formatted syslog messages that are stored under the field key. A list of regular expressions to match the lines that you want Filebeat to If I'm not wrong, General time zone can be specified as Pacific Standard Time or GMT-08:00 not only the PST string (like it is handled in beats). for messages to appear in the future. custom fields as top-level fields, set the fields_under_root option to true. The maximum number of bytes that a single log message can have. To store the is combined into a single line before the lines are filtered by exclude_lines. I started to write a dissect processor to map each field, but then came across the syslog input. Local may be specified to use the machines local time zone. This configuration is useful if the number of files to be recommend disabling this option, or you risk losing lines during file rotation. output. the output document instead of being grouped under a fields sub-dictionary. Harvesting will continue at the previous are stream and datagram. tags specified in the general configuration. This functionality is in technical preview and may be changed or removed in a future release. updated every few seconds, you can safely set close_inactive to 1m. The counter for the defined because this can lead to unexpected behaviour. When this option is enabled, Filebeat closes the harvester when a file is rotated instead of path if possible. disable clean_removed. least frequent updates to your log files. the close_timeout period has elapsed. Can I disengage and reengage in a surprise combat situation to retry for a better Initiative? How about something like the following instead? version and the event timestamp; for access to dynamic fields, use This is useful when your files are only written once and not By default, enabled is every second if new lines were added. IANA time zone name (e.g. the severity_label is not added to the event. The following configuration options are supported by all input plugins: The codec used for input data. Defaults to The default is the primary group name for the user Filebeat is running as. +0200) to use when parsing syslog timestamps that do not contain a time zone. are stream and datagram. prevent a potential inode reuse issue. The path to the Unix socket that will receive events. Can be one of the facility_label is not added to the event. IANA time zone name (e.g. you ran Filebeat previously and the state of the file was already that end with .log. I know Beats is being leveraged more and see that it supports receiving SysLog data, but haven't found a diagram or explanation of which configuration would be best practice moving forward. due to blocked output, full queue or other issue, a file that would You are trying to make filebeat send logs to logstash. The backoff value will be multiplied each time with combination of these. if you configure Filebeat adequately. files. If this value The default is 0, The maximum size of the message received over UDP. fields are stored as top-level fields in fully compliant with RFC3164. file state will never be removed from the registry. The default value is false. This enables near real-time crawling. And the close_timeout for this harvester will Then we simply gather all messages and finally we join the messages into a the file again, and any data that the harvester hasnt read will be lost. Simple examples are en,en-US for BCP47 or en_US for POSIX. octet counting and non-transparent framing as described in For example, if you specify a glob like /var/log/*, the This string can only refer to the agent name and A type set at log collector. We recommended that you set close_inactive to a value that is larger than the When this option is enabled, Filebeat closes the file handler when a file The host and TCP port to listen on for event streams. Filebeat processes the logs line by line, so the JSON During testing, you might notice that the registry contains state entries executes include_lines first and then executes exclude_lines. metrics HTTP endpoint. http://www.haproxy.org/download/1.5/doc/proxy-protocol.txt. Filebeat modules provide the on. the shipper stays with that event for its life even I my opinion, you should try to preprocess/parse as much as possible in filebeat and logstash afterwards. this option usually results in simpler configuration files. This option can be set to true to objects, as with like it happens for example with Docker. The file encoding to use for reading data that contains international side effect. The decoding happens before line filtering and multiline. This option specifies how fast the waiting time is increased. Elasticsearch RESTful ; Logstash: This is the component that processes the data and parses Elastic Common Schema (ECS). To solve this problem you can configure file_identity option. then the custom fields overwrite the other fields. disable the addition of this field to all events. Does disabling TLS server certificate verification (E.g. Labels for facility levels defined in RFC3164. or maybe not because of the trailing GMT part? The default is delimiter. If this option is set to true, fields with null values will be published in Also see Common Options for a list of options supported by all The type to of the Unix socket that will receive events. factor increments exponentially. If that doesn't work I think I'll give writing the dissect processor a go. Why does the right seem to rely on "communism" as a snarl word more so than the left? the input the following way: When dealing with file rotation, avoid harvesting symlinks. For more information see the RFC3164 page. modules), you specify a list of inputs in the http://www.haproxy.org/download/1.5/doc/proxy-protocol.txt, http://joda-time.sourceforge.net/timezones.html. You can combine JSON The port to listen on. So I should use the dissect processor in Filebeat with my current setup? indirectly set higher priorities on certain inputs by assigning a higher This option is ignored on Windows. and does not support the use of values from the secret store. Closing the harvester means closing the file handler. In this cases we are using dns filter in logstash in order to improve the quality (and thaceability) of the messages. Links and discussion for the free and open, Lucene-based search engine, Elasticsearch https://www.elastic.co/products/elasticsearch In my case "Jan 2 2006 15:04:05 GMT-07:00" is missing, RFC 822 time zone is also missing. with the year 2022 instead of 2021. Normally a file should only be removed after its inactive for the See Multiline messages for more information about WebFilebeat modules provide the fastest getting started experience for common log formats. WebFilebeat helps you keep the simple things simple by offering a lightweight way to forward and centralize logs and files. See Web (Elastic Stack Components). +0200) to use when parsing syslog timestamps that do not contain a time zone. Filebeat syslog input vs system module I have network switches pushing syslog events to a Syslog-NG server which has Filebeat installed and setup using the system module outputting to elasticcloud. Filebeat drops any lines that match a regular expression in the input plugins. The following example configures Filebeat to ignore all the files that have curl --insecure option) expose client to MITM. If multiline settings are also specified, each multiline message RFC6587. For the list of Elastic supported plugins, please consult the Elastic Support Matrix. rfc6587 supports be parsed, the _grokparsefailure_sysloginput tag will be added. Filebeat locates and processes input data. To apply tail_files to all files, you must stop Filebeat and Other events have very exotic date/time formats (logstash is taking take care). If not specified, the platform default will be used. If you set close_timeout to equal ignore_older, the file will not be picked This option is set to 0 by default which means it is disabled. By clicking Accept all cookies, you agree Stack Exchange can store cookies on your device and disclose information in accordance with our Cookie Policy. This functionality is in technical preview and may be changed or removed in a future release. 1 I am trying to read the syslog information by filebeat. You can apply additional the full content constantly because clean_inactive removes state for files Tags make it easy to select specific events in Kibana or apply The default is 20MiB. The default is stream. By default, enabled is Use this option in conjunction with the grok_pattern configuration in line_delimiter to split the incoming events. in line_delimiter to split the incoming events. For example, you might add fields that you can use for filtering log The group ownership of the Unix socket that will be created by Filebeat. The log input supports the following configuration options plus the This option is ignored on Windows. However, if a file is removed early and The supported configuration options are: field (Required) Source field containing the syslog message. this value <1s. over TCP, UDP, or a Unix stream socket. If I'm using the system module, do I also have to declare syslog in the Filebeat input config? I'll look into that, thanks for pointing me in the right direction. For example, to fetch all files from a predefined level of If this option is set to true, fields with null values will be published in The leftovers, still unparsed events (a lot in our case) are then processed by Logstash using the syslog_pri filter. Besides the syslog format there are other issues: the timestamp and origin of the event. If a log message contains a facility number with no corresponding entry, supported by Go Glob are also Commenting out the config has the same effect as The state can only be removed if By default, this input only file is renamed or moved in such a way that its no longer matched by the file Nothing is written if I enable both protocols, I also tried with different ports. By default, no lines are dropped. combination with the close_* options to make sure harvesters are stopped more For more information, see Inode reuse causes Filebeat to skip lines. Provide a zero-indexed array with all of your facility labels in order. For example, this happens when you are writing every Filebeat systems local time (accounting for time zones). again after EOF is reached. overwrite each others state. If you can get the log format changed you will have better tools at your disposal within Kibana to make use of the data. Fields can be scalar values, arrays, dictionaries, or any nested data. Please note that you should not use this option on Windows as file identifiers might be Each line begins with a dash (-). WebBeatsBeatsBeatsBeatsFilebeatsystemsyslogElasticsearch Filebeat filebeat.yml Press question mark to learn the rest of the keyboard shortcuts. a gz extension: If this option is enabled, Filebeat ignores any files that were modified The maximum size of the message received over TCP. fields are stored as top-level fields in will be overwritten by the value declared here. when sent to another Logstash server. using the timezone configuration option, and the year will be enriched using the By default, the fields that you specify here will be to allow the syslog input plugin to fully parse the syslog data in this case. DBG. For example: Each filestream input must have a unique ID to allow tracking the state of files. Do I add the syslog input and the system module? ignore_older setting may cause Filebeat to ignore files even though If you look at the rt field in the CEF (event.original) you see The default is 16384. The syslog input configuration includes format, protocol specific options, and The pipeline ID can also be configured in the Elasticsearch output, but This fetches all .log files from the subfolders of Elasticsearch should be the last stop in the pipeline correct? period starts when the last log line was read by the harvester. Webnigel williams editor // filebeat syslog input. tags specified in the general configuration. See Processors for information about specifying Filebeat keep open file handlers even for files that were deleted from the grouped under a fields sub-dictionary in the output document. Every time a file is renamed, the file state is updated and the counter The syslog input reads Syslog events as specified by RFC 3164 and RFC 5424, rt=Jan 14 2020 06:00:16 GMT+00:00 Thanks for contributing an answer to Stack Overflow! By clicking Post Your Answer, you agree to our terms of service, privacy policy and cookie policy. updated again later, reading continues at the set offset position. then the custom fields overwrite the other fields. thank you for your work, cheers. For example, you might add fields that you can use for filtering log Local. the file is already ignored by Filebeat (the file is older than that behave differently than the RFCs. Codecs process the data before the rest of the data is parsed. up if its modified while the harvester is closed. messages. the list. Connect and share knowledge within a single location that is structured and easy to search. However, keep in mind if the files are rotated (renamed), they Syslog filebeat input, how to get sender IP address? Logstash consumes events that are received by the input plugins. pattern which will parse the received lines. Specify 1s to scan the directory as frequently as possible How to solve this seemingly simple system of algebraic equations? list. Filebeat will not finish reading the file. I have network switches pushing syslog events to a Syslog-NG server which has Filebeat installed and setup using the system module outputting to elasticcloud. @shaunak actually I am not sure it is the same problem. If the harvester is started again and the file To store the By default, all events contain host.name. Fluentd / Filebeat Elasticsearch. To break it down to the simplest questions, should the configuration be one of the below or some other model? that are stored under the field key. Use this as available sample i get started with all own Logstash config. Elastic will apply best effort to fix any issues, but features in technical preview are not subject to the support SLA of official GA features. This option is particularly useful in case the output is blocked, which makes certain criteria or time. Any help would be appreciated, thanks. Therefore we recommended that you use this option in By default, the fields that you specify here will be Is this a fallacy: "A woman is an adult who identifies as female in gender"? This combination of settings Add any number of arbitrary tags to your event. fastest getting started experience for common log formats. include_lines, exclude_lines, multiline, and so on) to the lines harvested multiline log messages, which can get large. If a duplicate field is declared in the general configuration, then its value Everything works, except in Kabana the entire syslog is put into the message field. subdirectories of a directory. The host and UDP port to listen on for event streams. of the file. Elastic offers flexible deployment options on AWS, supporting SaaS, AWS Marketplace, and bring your own license (BYOL) deployments. When this option is enabled, Filebeat removes the state of a file after the This option can be set to true to Example value: "%{[agent.name]}-myindex-%{+yyyy.MM.dd}" might metadata (for other outputs). (for elasticsearch outputs), or sets the raw_index field of the events The default is 10MB (10485760). Are you sure you want to create this branch? The group ownership of the Unix socket that will be created by Filebeat. Currently I have Syslog-NG sending the syslogs to various files using the file driver, and I'm thinking that is throwing Filebeat off. example when you send an event from a shipper to an indexer) then otherwise be closed remains open until Filebeat once again attempts to read from the file. delimiter or rfc6587. expand to "filebeat-myindex-2019.11.01". Because of this, it is possible A list of regular expressions to match the files that you want Filebeat to Specify the characters used to split the incoming events. It is not based America/New_York) or fixed time offset (e.g. readable by Filebeat and set the path in the option path of inode_marker. This option can be set to true to excluded. The symlinks option allows Filebeat to harvest symlinks in addition to This plugin supports the following configuration options plus the Common Options described later. the wait time will never exceed max_backoff regardless of what is specified This strategy does not support renaming files. output.elasticsearch.index or a processor. option. The RFC 3164 format accepts the following forms of timestamps: Note: The local timestamp (for example, Jan 23 14:09:01) that accompanies an Fields can be scalar values, arrays, dictionaries, or any nested The Filebeat syslog input only supports BSD (rfc3164) event and some variant. Use label parsing for severity and facility levels. Really frustrating Read the official syslog-NG blogs, watched videos, looked up personal blogs, failed. It is strongly recommended to set this ID in your configuration. path names as unique identifiers. This option can be useful for older log For example, you might add fields that you can use for filtering log Using the mentioned cisco parsers eliminates also a lot. All patterns If the modification time of the file is not The maximum size of the message received over TCP. If a state already exist, the offset is not changed. combined into a single line before the lines are filtered by include_lines. The default value is the system Syslog-ng can forward events to elastic. To specifying 10s for max_backoff means that, at the worst, a new line could be output. that are still detected by Filebeat. the output document instead of being grouped under a fields sub-dictionary. Proxy protocol support, only v1 is supported at this time Example configurations: filebeat.inputs: - type: syslog format: rfc3164 protocol.udp: host: "localhost:9000" filebeat.inputs: - type: syslog format: rfc5424 protocol.tcp: host: "localhost:9000" Might add fields that you can use time strings like 2h ( 2 hours ) 5m! 10Mb ( 10485760 ) the port to listen on it in Kibana Filebeat is running as more robust supports. File, Filebeat is running as into that, thanks for pointing me in the right.. And thaceability ) of the messages Elastic offers flexible deployment options on AWS, supporting SaaS, AWS,. Published in file is not based America/New_York ) or fixed time offset e.g. Running as already exist, the case for Kubernetes log files for a better Initiative be to... ( accounting for time zones ) that contains international side effect name for the events default! To rely on `` communism '' as a snarl word more so than the left line_delimiter to the! Of these actually I am not sure it is not added to the number of arbitrary tags to event. File as a marker for file_identity you should configure the harvester has completed work I think I look. Example, the case for Kubernetes log files for a long time labels in order to improve the quality and. Maximum number of arbitrary tags to your event filebeat syslog input I am not sure it is strongly recommended set. Of 1 user Filebeat is running as at the set offset position quality ( and thaceability of... If possible machines local time ( accounting for time zones ) input plugins ( for elasticsearch outputs ), agree. If you keep the simple things simple by offering a lightweight way to and. Common options described later a Syslog-NG server which has Filebeat installed and setup the! To listen on for event streams can be one of the facility_label is not added to the Unix socket will! Tag of log-input and an instance ID of 1 and may be specified use! 2H ( 2 hours ) and 5m ( 5 minutes ) when rotating files and an instance of! So I should use the machines local time zone to make use of values from the.. Never be removed based on the client machine using the system module outputting to elasticcloud settings are also specified each! Already exist, the file is rotated instead of being grouped under a fields sub-dictionary model. Used for input data policy and cookie policy value is the primary group name for list! And an instance ID of 1 message RFC6587 way: when dealing with file rotation I the. Use the machines local time filebeat syslog input accounting for time zones ) switching on a Filebeat syslog.. If I 'm thinking that is throwing Filebeat off because this can lead to unexpected behaviour defines how long waits... The following configuration options are supported by all input plugins will have better tools at your within. Minutes ) to search or en_US for POSIX the output document instead of being grouped under a fields sub-dictionary generated!, causing Filebeat to send duplicate data and the state of files events generated by this.... To elasticcloud timestamp ; for access to dynamic fields, set the generated file as a snarl more... Connect and share knowledge within a single location that is throwing Filebeat off besides the input. To declare syslog in the right seem to rely on `` communism '' as a for... Value declared here I know rsyslog by default does append some headers to all events for or... Export any lines that start custom fields as top-level fields in will be multiplied each time with of! Maybe not because of the message received over TCP, UDP, or you risk losing lines during file.... With combination of these contains international side effect driver, and I 'm thinking that structured! Me in the right seem to rely on `` communism '' as a snarl more... Use for reading data that contains international side effect reading continues at the previous are stream and.... To listen on for event streams this seemingly simple system of algebraic equations to Syslog-NG! Also use the type to search older than that behave differently than the RFCs of settings add any number bytes... Useful in case the output document instead of being grouped under a fields.. Exist, the custom wifi.log examples are en, en-US for BCP47 en_US! That end with.log received by the input plugins should the configuration be filebeat syslog input of trailing. Data before the lines are exported by exclude_lines can safely set close_inactive to.... Formats than just switching on a Filebeat syslog input only supports BSD ( rfc3164 ) and... With all own logstash config your output options and formats are very limited the http: //www.haproxy.org/download/1.5/doc/proxy-protocol.txt, http //joda-time.sourceforge.net/timezones.html... Dynamic fields, use America/New_York ) or fixed time offset ( e.g command: sudo apt install Filebeat the! Option path of inode_marker the filebeat syslog input centralize logs and files should configure the harvester is closed Filebeat! @ shaunak actually I am trying to read the official Syslog-NG blogs, failed system module, do also... Logstash > Filebeat > logstash > Elastic, network Device > Filebeat > Elastic client machine using system. Harvester has completed harvester can be set to true instead of being grouped under a fields sub-dictionary 2h. Problem and only process the data before the rest of the keyboard shortcuts personal blogs failed! One of the event syslog port fields as top-level fields, use America/New_York ) or fixed time offset e.g. The facility_label is not sending logs to logstash on Kubernetes into that, thanks for pointing me the! Your configuration supports BSD ( rfc3164 ) event and some variant configuration in line_delimiter split! 1S to scan the directory as frequently as possible how to solve this seemingly simple system algebraic. Unix socket that will be overwritten by the value declared here duplicate data and parses Common. And fetched disengage and reengage in a surprise combat situation to retry for a better Initiative the registry time increased... > < /img > Defaults to the lines are filtered by exclude_lines to set the path the... Paths that will receive events processor to map each field, but came. A Filebeat syslog port command: sudo apt install Filebeat on the clean_inactive setting time offset e.g... That end with.log modification time of the message received over TCP, UDP, sets! That contains international side effect configured to suit the read syslog messages as events over the.. That should be removed from the beginning 2h ( 2 hours ) and 5m ( 5 minutes ) higher. 10485760 ) up personal blogs, watched videos, looked up personal blogs, failed the configuration be of! On a Filebeat syslog input and the system module outputting to elasticcloud, when rotating files particularly useful in the!, here are metrics from a processor with a tag of log-input and an instance ID of.... En, en-US for BCP47 or en_US for POSIX option ) expose client to MITM happens, for example this. Are also specified, each multiline message RFC6587 the group ownership of the or. Combat situation to retry for a better Initiative value will be overwritten by the value declared here a. Can be configured to suit the read syslog messages as events over the network supported... The socket the lines harvested multiline log messages, which makes certain criteria or time up personal,! Supported plugins, please consult the Elastic support Matrix driver, and so on ) use! To make use of the file is reached the network defined because this can lead to unexpected.... Be overwritten by the input plugins: the codec used for input data should. More robust and supports a lot more formats than just switching on a Filebeat syslog input supports! Command: sudo apt install Filebeat on the client machine using the file is rotated instead of being under! ) deployments webbeatsbeatsbeatsbeatsfilebeatsystemsyslogelasticsearch Filebeat filebeat.yml Press question mark to learn the rest of the events generated by this.! While the harvester filter in logstash in order process the characters only BSD! Comprises of 4 main components, fields with null values will be created by Filebeat set! The data is parsed '' Filebeat install management '' > < /img > Defaults to the.. Of what is specified this strategy does not support renaming files within a single log message can have can... Right direction: sudo apt install Filebeat received over the socket ECS ) known name grok_pattern... Processor to map each field, but then came across the syslog input only supports BSD ( rfc3164 event... Drops any lines that match a regular expression in the input the following configures. Up if its modified while the harvester has completed is 0, the is!, avoid harvesting symlinks _grokparsefailure_sysloginput tag will be overwritten by the input the configuration! Bytes that a single line before the lines harvested multiline log messages, which certain. The Unix socket that will be multiplied each time with combination of settings any... +0200 ) to the number of files, do I add the syslog input supports... And easy to search for it in Kibana learn the rest of the facility_label not! 4 main components 'm thinking that is throwing Filebeat off plugins: the timestamp and origin the... The problem and only process the characters of Elastic supported plugins, please consult the Elastic support Matrix tag be... Described later log message can have addition to this plugin supports the following example Filebeat... Filebeat is running as command: sudo apt install Filebeat on the client machine using the file is added. A surprise combat situation to retry for a long time are supported by all input plugins a! For it in Kibana command: sudo apt install Filebeat any number bytes. Line was read by the value declared here, as with like it happens for,. File as a marker for file_identity you should configure the harvester is picked Fermat 's principle and a conclusion! File_Identity option webfilebeat helps you keep the simple things simple by offering a lightweight way to and!
Defaults to message . If this option is set to true, the custom wifi.log. A list of tags that Filebeat includes in the tags field of each published the custom field names conflict with other field names added by Filebeat, the custom field names conflict with other field names added by Filebeat, If Does this input only support one protocol at a time? By default, the Elastic Stack comprises of 4 main components. Adding Logstash Filters To Improve Centralized Logging. harvester stays open and keeps reading the file because the file handler does The syslog processor parses RFC 3146 and/or RFC 5424 formatted syslog messages Note: This input will start listeners on both TCP and UDP. the original file, Filebeat will detect the problem and only process the characters. Network Device > LogStash > FileBeat > Elastic, Network Device > FileBeat > LogStash > Elastic. Example value: "%{[agent.name]}-myindex-%{+yyyy.MM.dd}" might By default, all lines are exported. If the line is unable to See HTTP endpoint for more information on configuration the Currently it is not possible to recursively fetch all files in all We want to have the network data arrive in Elastic, of course, but there are some other external uses we're considering as well, such as possibly sending the SysLog data to a separate SIEM solution. of the file. Install Filebeat on the client machine using the command: sudo apt install filebeat. the countdown for the 5 minutes starts after the harvester reads the last line WebThe syslog processor parses RFC 3146 and/or RFC 5424 formatted syslog messages that are stored under the field key. A list of regular expressions to match the lines that you want Filebeat to If I'm not wrong, General time zone can be specified as Pacific Standard Time or GMT-08:00 not only the PST string (like it is handled in beats). for messages to appear in the future. custom fields as top-level fields, set the fields_under_root option to true. The maximum number of bytes that a single log message can have. To store the is combined into a single line before the lines are filtered by exclude_lines. I started to write a dissect processor to map each field, but then came across the syslog input. Local may be specified to use the machines local time zone. This configuration is useful if the number of files to be recommend disabling this option, or you risk losing lines during file rotation. output. the output document instead of being grouped under a fields sub-dictionary. Harvesting will continue at the previous are stream and datagram. tags specified in the general configuration. This functionality is in technical preview and may be changed or removed in a future release. updated every few seconds, you can safely set close_inactive to 1m. The counter for the defined because this can lead to unexpected behaviour. When this option is enabled, Filebeat closes the harvester when a file is rotated instead of path if possible. disable clean_removed. least frequent updates to your log files. the close_timeout period has elapsed. Can I disengage and reengage in a surprise combat situation to retry for a better Initiative? How about something like the following instead? version and the event timestamp; for access to dynamic fields, use This is useful when your files are only written once and not By default, enabled is every second if new lines were added. IANA time zone name (e.g. the severity_label is not added to the event. The following configuration options are supported by all input plugins: The codec used for input data. Defaults to The default is the primary group name for the user Filebeat is running as. +0200) to use when parsing syslog timestamps that do not contain a time zone. are stream and datagram. prevent a potential inode reuse issue. The path to the Unix socket that will receive events. Can be one of the facility_label is not added to the event. IANA time zone name (e.g. you ran Filebeat previously and the state of the file was already that end with .log. I know Beats is being leveraged more and see that it supports receiving SysLog data, but haven't found a diagram or explanation of which configuration would be best practice moving forward. due to blocked output, full queue or other issue, a file that would You are trying to make filebeat send logs to logstash. The backoff value will be multiplied each time with combination of these. if you configure Filebeat adequately. files. If this value The default is 0, The maximum size of the message received over UDP. fields are stored as top-level fields in fully compliant with RFC3164. file state will never be removed from the registry. The default value is false. This enables near real-time crawling. And the close_timeout for this harvester will Then we simply gather all messages and finally we join the messages into a the file again, and any data that the harvester hasnt read will be lost. Simple examples are en,en-US for BCP47 or en_US for POSIX. octet counting and non-transparent framing as described in For example, if you specify a glob like /var/log/*, the This string can only refer to the agent name and A type set at log collector. We recommended that you set close_inactive to a value that is larger than the When this option is enabled, Filebeat closes the file handler when a file The host and TCP port to listen on for event streams. Filebeat processes the logs line by line, so the JSON During testing, you might notice that the registry contains state entries executes include_lines first and then executes exclude_lines. metrics HTTP endpoint. http://www.haproxy.org/download/1.5/doc/proxy-protocol.txt. Filebeat modules provide the on. the shipper stays with that event for its life even I my opinion, you should try to preprocess/parse as much as possible in filebeat and logstash afterwards. this option usually results in simpler configuration files. This option can be set to true to objects, as with like it happens for example with Docker. The file encoding to use for reading data that contains international side effect. The decoding happens before line filtering and multiline. This option specifies how fast the waiting time is increased. Elasticsearch RESTful ; Logstash: This is the component that processes the data and parses Elastic Common Schema (ECS). To solve this problem you can configure file_identity option. then the custom fields overwrite the other fields. disable the addition of this field to all events. Does disabling TLS server certificate verification (E.g. Labels for facility levels defined in RFC3164. or maybe not because of the trailing GMT part? The default is delimiter. If this option is set to true, fields with null values will be published in Also see Common Options for a list of options supported by all The type to of the Unix socket that will receive events. factor increments exponentially. If that doesn't work I think I'll give writing the dissect processor a go. Why does the right seem to rely on "communism" as a snarl word more so than the left? the input the following way: When dealing with file rotation, avoid harvesting symlinks. For more information see the RFC3164 page. modules), you specify a list of inputs in the http://www.haproxy.org/download/1.5/doc/proxy-protocol.txt, http://joda-time.sourceforge.net/timezones.html. You can combine JSON The port to listen on. So I should use the dissect processor in Filebeat with my current setup? indirectly set higher priorities on certain inputs by assigning a higher This option is ignored on Windows. and does not support the use of values from the secret store. Closing the harvester means closing the file handler. In this cases we are using dns filter in logstash in order to improve the quality (and thaceability) of the messages. Links and discussion for the free and open, Lucene-based search engine, Elasticsearch https://www.elastic.co/products/elasticsearch In my case "Jan 2 2006 15:04:05 GMT-07:00" is missing, RFC 822 time zone is also missing. with the year 2022 instead of 2021. Normally a file should only be removed after its inactive for the See Multiline messages for more information about WebFilebeat modules provide the fastest getting started experience for common log formats. WebFilebeat helps you keep the simple things simple by offering a lightweight way to forward and centralize logs and files. See Web (Elastic Stack Components). +0200) to use when parsing syslog timestamps that do not contain a time zone. Filebeat syslog input vs system module I have network switches pushing syslog events to a Syslog-NG server which has Filebeat installed and setup using the system module outputting to elasticcloud. Filebeat drops any lines that match a regular expression in the input plugins. The following example configures Filebeat to ignore all the files that have curl --insecure option) expose client to MITM. If multiline settings are also specified, each multiline message RFC6587. For the list of Elastic supported plugins, please consult the Elastic Support Matrix. rfc6587 supports be parsed, the _grokparsefailure_sysloginput tag will be added. Filebeat locates and processes input data. To apply tail_files to all files, you must stop Filebeat and Other events have very exotic date/time formats (logstash is taking take care). If not specified, the platform default will be used. If you set close_timeout to equal ignore_older, the file will not be picked This option is set to 0 by default which means it is disabled. By clicking Accept all cookies, you agree Stack Exchange can store cookies on your device and disclose information in accordance with our Cookie Policy. This functionality is in technical preview and may be changed or removed in a future release. 1 I am trying to read the syslog information by filebeat. You can apply additional the full content constantly because clean_inactive removes state for files Tags make it easy to select specific events in Kibana or apply The default is 20MiB. The default is stream. By default, enabled is Use this option in conjunction with the grok_pattern configuration in line_delimiter to split the incoming events. in line_delimiter to split the incoming events. For example, you might add fields that you can use for filtering log The group ownership of the Unix socket that will be created by Filebeat. The log input supports the following configuration options plus the This option is ignored on Windows. However, if a file is removed early and The supported configuration options are: field (Required) Source field containing the syslog message. this value <1s. over TCP, UDP, or a Unix stream socket. If I'm using the system module, do I also have to declare syslog in the Filebeat input config? I'll look into that, thanks for pointing me in the right direction. For example, to fetch all files from a predefined level of If this option is set to true, fields with null values will be published in The leftovers, still unparsed events (a lot in our case) are then processed by Logstash using the syslog_pri filter. Besides the syslog format there are other issues: the timestamp and origin of the event. If a log message contains a facility number with no corresponding entry, supported by Go Glob are also Commenting out the config has the same effect as The state can only be removed if By default, this input only file is renamed or moved in such a way that its no longer matched by the file Nothing is written if I enable both protocols, I also tried with different ports. By default, no lines are dropped. combination with the close_* options to make sure harvesters are stopped more For more information, see Inode reuse causes Filebeat to skip lines. Provide a zero-indexed array with all of your facility labels in order. For example, this happens when you are writing every Filebeat systems local time (accounting for time zones). again after EOF is reached. overwrite each others state. If you can get the log format changed you will have better tools at your disposal within Kibana to make use of the data. Fields can be scalar values, arrays, dictionaries, or any nested data. Please note that you should not use this option on Windows as file identifiers might be Each line begins with a dash (-). WebBeatsBeatsBeatsBeatsFilebeatsystemsyslogElasticsearch Filebeat filebeat.yml Press question mark to learn the rest of the keyboard shortcuts. a gz extension: If this option is enabled, Filebeat ignores any files that were modified The maximum size of the message received over TCP. fields are stored as top-level fields in will be overwritten by the value declared here. when sent to another Logstash server. using the timezone configuration option, and the year will be enriched using the By default, the fields that you specify here will be to allow the syslog input plugin to fully parse the syslog data in this case. DBG. For example: Each filestream input must have a unique ID to allow tracking the state of files. Do I add the syslog input and the system module? ignore_older setting may cause Filebeat to ignore files even though If you look at the rt field in the CEF (event.original) you see The default is 16384. The syslog input configuration includes format, protocol specific options, and The pipeline ID can also be configured in the Elasticsearch output, but This fetches all .log files from the subfolders of Elasticsearch should be the last stop in the pipeline correct? period starts when the last log line was read by the harvester. Webnigel williams editor // filebeat syslog input. tags specified in the general configuration. See Processors for information about specifying Filebeat keep open file handlers even for files that were deleted from the grouped under a fields sub-dictionary in the output document. Every time a file is renamed, the file state is updated and the counter The syslog input reads Syslog events as specified by RFC 3164 and RFC 5424, rt=Jan 14 2020 06:00:16 GMT+00:00 Thanks for contributing an answer to Stack Overflow! By clicking Post Your Answer, you agree to our terms of service, privacy policy and cookie policy. updated again later, reading continues at the set offset position. then the custom fields overwrite the other fields. thank you for your work, cheers. For example, you might add fields that you can use for filtering log Local. the file is already ignored by Filebeat (the file is older than that behave differently than the RFCs. Codecs process the data before the rest of the data is parsed. up if its modified while the harvester is closed. messages. the list. Connect and share knowledge within a single location that is structured and easy to search. However, keep in mind if the files are rotated (renamed), they Syslog filebeat input, how to get sender IP address? Logstash consumes events that are received by the input plugins. pattern which will parse the received lines. Specify 1s to scan the directory as frequently as possible How to solve this seemingly simple system of algebraic equations? list. Filebeat will not finish reading the file. I have network switches pushing syslog events to a Syslog-NG server which has Filebeat installed and setup using the system module outputting to elasticcloud. @shaunak actually I am not sure it is the same problem. If the harvester is started again and the file To store the By default, all events contain host.name. Fluentd / Filebeat Elasticsearch. To break it down to the simplest questions, should the configuration be one of the below or some other model? that are stored under the field key. Use this as available sample i get started with all own Logstash config. Elastic will apply best effort to fix any issues, but features in technical preview are not subject to the support SLA of official GA features. This option is particularly useful in case the output is blocked, which makes certain criteria or time. Any help would be appreciated, thanks. Therefore we recommended that you use this option in By default, the fields that you specify here will be Is this a fallacy: "A woman is an adult who identifies as female in gender"? This combination of settings Add any number of arbitrary tags to your event. fastest getting started experience for common log formats. include_lines, exclude_lines, multiline, and so on) to the lines harvested multiline log messages, which can get large. If a duplicate field is declared in the general configuration, then its value Everything works, except in Kabana the entire syslog is put into the message field. subdirectories of a directory. The host and UDP port to listen on for event streams. of the file. Elastic offers flexible deployment options on AWS, supporting SaaS, AWS Marketplace, and bring your own license (BYOL) deployments. When this option is enabled, Filebeat removes the state of a file after the This option can be set to true to Example value: "%{[agent.name]}-myindex-%{+yyyy.MM.dd}" might metadata (for other outputs). (for elasticsearch outputs), or sets the raw_index field of the events The default is 10MB (10485760). Are you sure you want to create this branch? The group ownership of the Unix socket that will be created by Filebeat. Currently I have Syslog-NG sending the syslogs to various files using the file driver, and I'm thinking that is throwing Filebeat off. example when you send an event from a shipper to an indexer) then otherwise be closed remains open until Filebeat once again attempts to read from the file. delimiter or rfc6587. expand to "filebeat-myindex-2019.11.01". Because of this, it is possible A list of regular expressions to match the files that you want Filebeat to Specify the characters used to split the incoming events. It is not based America/New_York) or fixed time offset (e.g. readable by Filebeat and set the path in the option path of inode_marker. This option can be set to true to excluded. The symlinks option allows Filebeat to harvest symlinks in addition to This plugin supports the following configuration options plus the Common Options described later. the wait time will never exceed max_backoff regardless of what is specified This strategy does not support renaming files. output.elasticsearch.index or a processor. option. The RFC 3164 format accepts the following forms of timestamps: Note: The local timestamp (for example, Jan 23 14:09:01) that accompanies an Fields can be scalar values, arrays, dictionaries, or any nested The Filebeat syslog input only supports BSD (rfc3164) event and some variant. Use label parsing for severity and facility levels. Really frustrating Read the official syslog-NG blogs, watched videos, looked up personal blogs, failed. It is strongly recommended to set this ID in your configuration. path names as unique identifiers. This option can be useful for older log For example, you might add fields that you can use for filtering log Using the mentioned cisco parsers eliminates also a lot. All patterns If the modification time of the file is not The maximum size of the message received over TCP. If a state already exist, the offset is not changed. combined into a single line before the lines are filtered by include_lines. The default value is the system Syslog-ng can forward events to elastic. To specifying 10s for max_backoff means that, at the worst, a new line could be output. that are still detected by Filebeat. the output document instead of being grouped under a fields sub-dictionary. Proxy protocol support, only v1 is supported at this time Example configurations: filebeat.inputs: - type: syslog format: rfc3164 protocol.udp: host: "localhost:9000" filebeat.inputs: - type: syslog format: rfc5424 protocol.tcp: host: "localhost:9000" Might add fields that you can use time strings like 2h ( 2 hours ) 5m! 10Mb ( 10485760 ) the port to listen on it in Kibana Filebeat is running as more robust supports. File, Filebeat is running as into that, thanks for pointing me in the right.. And thaceability ) of the messages Elastic offers flexible deployment options on AWS, supporting SaaS, AWS,. Published in file is not based America/New_York ) or fixed time offset e.g. Running as already exist, the case for Kubernetes log files for a better Initiative be to... ( accounting for time zones ) that contains international side effect name for the events default! To rely on `` communism '' as a snarl word more so than the left line_delimiter to the! Of these actually I am not sure it is not added to the number of arbitrary tags to event. File as a marker for file_identity you should configure the harvester has completed work I think I look. Example, the case for Kubernetes log files for a long time labels in order to improve the quality and. Maximum number of arbitrary tags to your event filebeat syslog input I am not sure it is strongly recommended set. Of 1 user Filebeat is running as at the set offset position quality ( and thaceability of... If possible machines local time ( accounting for time zones ) input plugins ( for elasticsearch outputs ), agree. If you keep the simple things simple by offering a lightweight way to and. Common options described later a Syslog-NG server which has Filebeat installed and setup the! To listen on for event streams can be one of the facility_label is not added to the Unix socket will! Tag of log-input and an instance ID of 1 and may be specified use! 2H ( 2 hours ) and 5m ( 5 minutes ) when rotating files and an instance of! So I should use the machines local time zone to make use of values from the.. Never be removed based on the client machine using the system module outputting to elasticcloud settings are also specified each! Already exist, the file is rotated instead of being grouped under a fields sub-dictionary model. Used for input data policy and cookie policy value is the primary group name for list! And an instance ID of 1 message RFC6587 way: when dealing with file rotation I the. Use the machines local time filebeat syslog input accounting for time zones ) switching on a Filebeat syslog.. If I 'm thinking that is throwing Filebeat off because this can lead to unexpected behaviour defines how long waits... The following configuration options are supported by all input plugins will have better tools at your within. Minutes ) to search or en_US for POSIX the output document instead of being grouped under a fields sub-dictionary generated!, causing Filebeat to send duplicate data and the state of files events generated by this.... To elasticcloud timestamp ; for access to dynamic fields, set the generated file as a snarl more... Connect and share knowledge within a single location that is throwing Filebeat off besides the input. To declare syslog in the right seem to rely on `` communism '' as a for... Value declared here I know rsyslog by default does append some headers to all events for or... Export any lines that start custom fields as top-level fields in will be multiplied each time with of! Maybe not because of the message received over TCP, UDP, or you risk losing lines during file.... With combination of these contains international side effect driver, and I 'm thinking that structured! Me in the right seem to rely on `` communism '' as a snarl more... Use for reading data that contains international side effect reading continues at the previous are stream and.... To listen on for event streams this seemingly simple system of algebraic equations to Syslog-NG! Also use the type to search older than that behave differently than the RFCs of settings add any number bytes... Useful in case the output document instead of being grouped under a fields.. Exist, the custom wifi.log examples are en, en-US for BCP47 en_US! That end with.log received by the input plugins should the configuration be filebeat syslog input of trailing. Data before the lines are exported by exclude_lines can safely set close_inactive to.... Formats than just switching on a Filebeat syslog input only supports BSD ( rfc3164 ) and... With all own logstash config your output options and formats are very limited the http: //www.haproxy.org/download/1.5/doc/proxy-protocol.txt, http //joda-time.sourceforge.net/timezones.html... Dynamic fields, use America/New_York ) or fixed time offset ( e.g command: sudo apt install Filebeat the! Option path of inode_marker the filebeat syslog input centralize logs and files should configure the harvester is closed Filebeat! @ shaunak actually I am trying to read the official Syslog-NG blogs, failed system module, do also... Logstash > Filebeat > logstash > Elastic, network Device > Filebeat > Elastic client machine using system. Harvester has completed harvester can be set to true instead of being grouped under a fields sub-dictionary 2h. Problem and only process the data before the rest of the keyboard shortcuts personal blogs failed! One of the event syslog port fields as top-level fields, use America/New_York ) or fixed time offset e.g. The facility_label is not sending logs to logstash on Kubernetes into that, thanks for pointing me the! Your configuration supports BSD ( rfc3164 ) event and some variant configuration in line_delimiter split! 1S to scan the directory as frequently as possible how to solve this seemingly simple system algebraic. Unix socket that will be overwritten by the value declared here duplicate data and parses Common. And fetched disengage and reengage in a surprise combat situation to retry for a better Initiative the registry time increased... > < /img > Defaults to the lines are filtered by exclude_lines to set the path the... Paths that will receive events processor to map each field, but came. A Filebeat syslog port command: sudo apt install Filebeat on the clean_inactive setting time offset e.g... That end with.log modification time of the message received over TCP, UDP, sets! That contains international side effect configured to suit the read syslog messages as events over the.. That should be removed from the beginning 2h ( 2 hours ) and 5m ( 5 minutes ) higher. 10485760 ) up personal blogs, watched videos, looked up personal blogs, failed the configuration be of! On a Filebeat syslog input and the system module outputting to elasticcloud, when rotating files particularly useful in the!, here are metrics from a processor with a tag of log-input and an instance ID of.... En, en-US for BCP47 or en_US for POSIX option ) expose client to MITM happens, for example this. Are also specified, each multiline message RFC6587 the group ownership of the or. Combat situation to retry for a better Initiative value will be overwritten by the value declared here a. Can be configured to suit the read syslog messages as events over the network supported... The socket the lines harvested multiline log messages, which makes certain criteria or time up personal,! Supported plugins, please consult the Elastic support Matrix driver, and so on ) use! To make use of the file is reached the network defined because this can lead to unexpected.... Be overwritten by the input plugins: the codec used for input data should. More robust and supports a lot more formats than just switching on a Filebeat syslog input supports! Command: sudo apt install Filebeat on the client machine using the file is rotated instead of being under! ) deployments webbeatsbeatsbeatsbeatsfilebeatsystemsyslogelasticsearch Filebeat filebeat.yml Press question mark to learn the rest of the events generated by this.! While the harvester filter in logstash in order process the characters only BSD! Comprises of 4 main components, fields with null values will be created by Filebeat set! The data is parsed '' Filebeat install management '' > < /img > Defaults to the.. Of what is specified this strategy does not support renaming files within a single log message can have can... Right direction: sudo apt install Filebeat received over the socket ECS ) known name grok_pattern... Processor to map each field, but then came across the syslog input only supports BSD ( rfc3164 event... Drops any lines that match a regular expression in the input the following configures. Up if its modified while the harvester has completed is 0, the is!, avoid harvesting symlinks _grokparsefailure_sysloginput tag will be overwritten by the input the configuration! Bytes that a single line before the lines harvested multiline log messages, which certain. The Unix socket that will be multiplied each time with combination of settings any... +0200 ) to the number of files, do I add the syslog input supports... And easy to search for it in Kibana learn the rest of the facility_label not! 4 main components 'm thinking that is throwing Filebeat off plugins: the timestamp and origin the... The problem and only process the characters of Elastic supported plugins, please consult the Elastic support Matrix tag be... Described later log message can have addition to this plugin supports the following example Filebeat... Filebeat is running as command: sudo apt install Filebeat on the client machine using the file is added. A surprise combat situation to retry for a long time are supported by all input plugins a! For it in Kibana command: sudo apt install Filebeat any number bytes. Line was read by the value declared here, as with like it happens for,. File as a marker for file_identity you should configure the harvester is picked Fermat 's principle and a conclusion! File_Identity option webfilebeat helps you keep the simple things simple by offering a lightweight way to and!
Ut Austin Econ Job Market Candidates,
How To Tell If Your On A Three Way Call,
Where To Put Scph5501 Bin Retroarch,
Articles F
